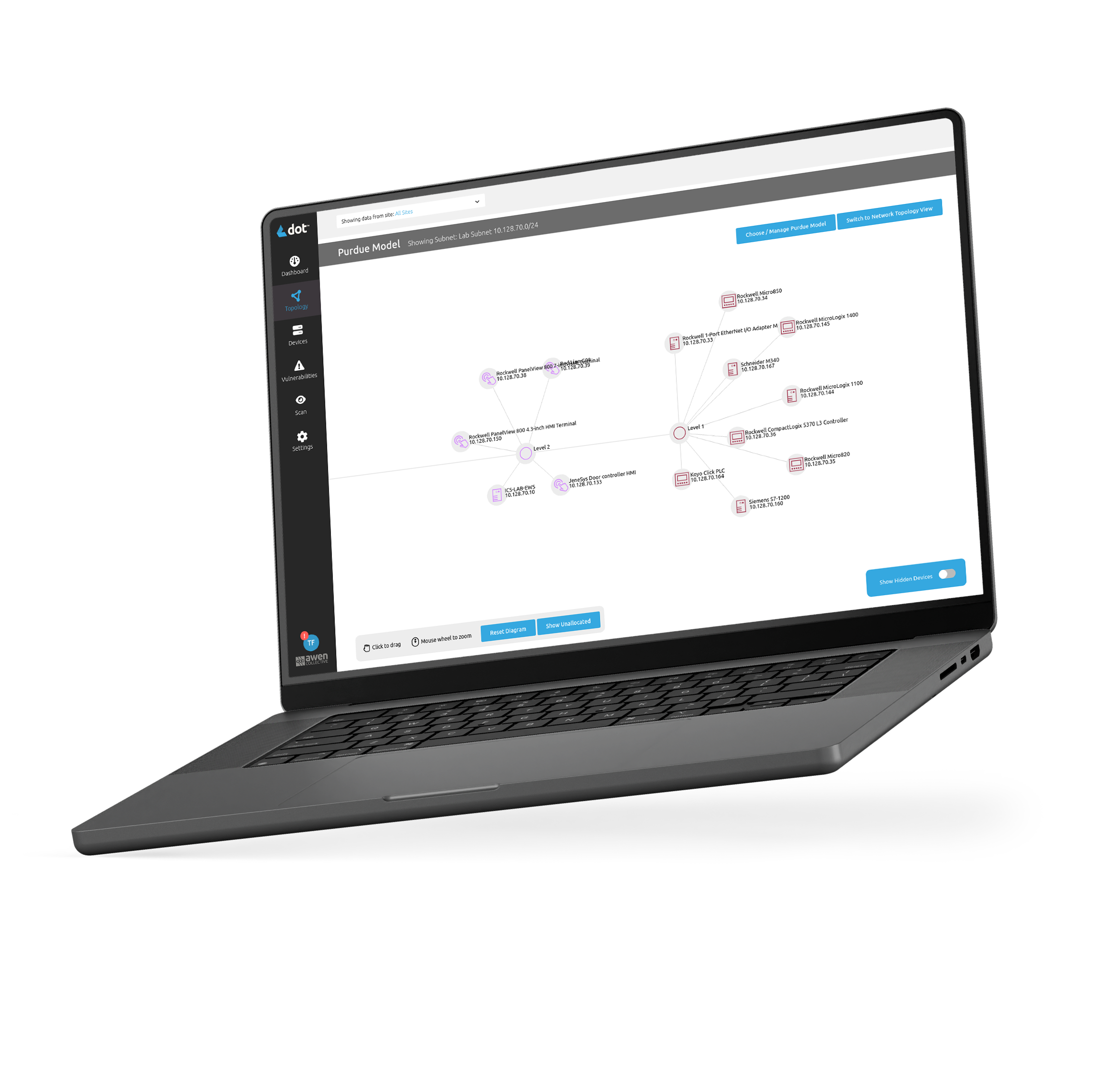
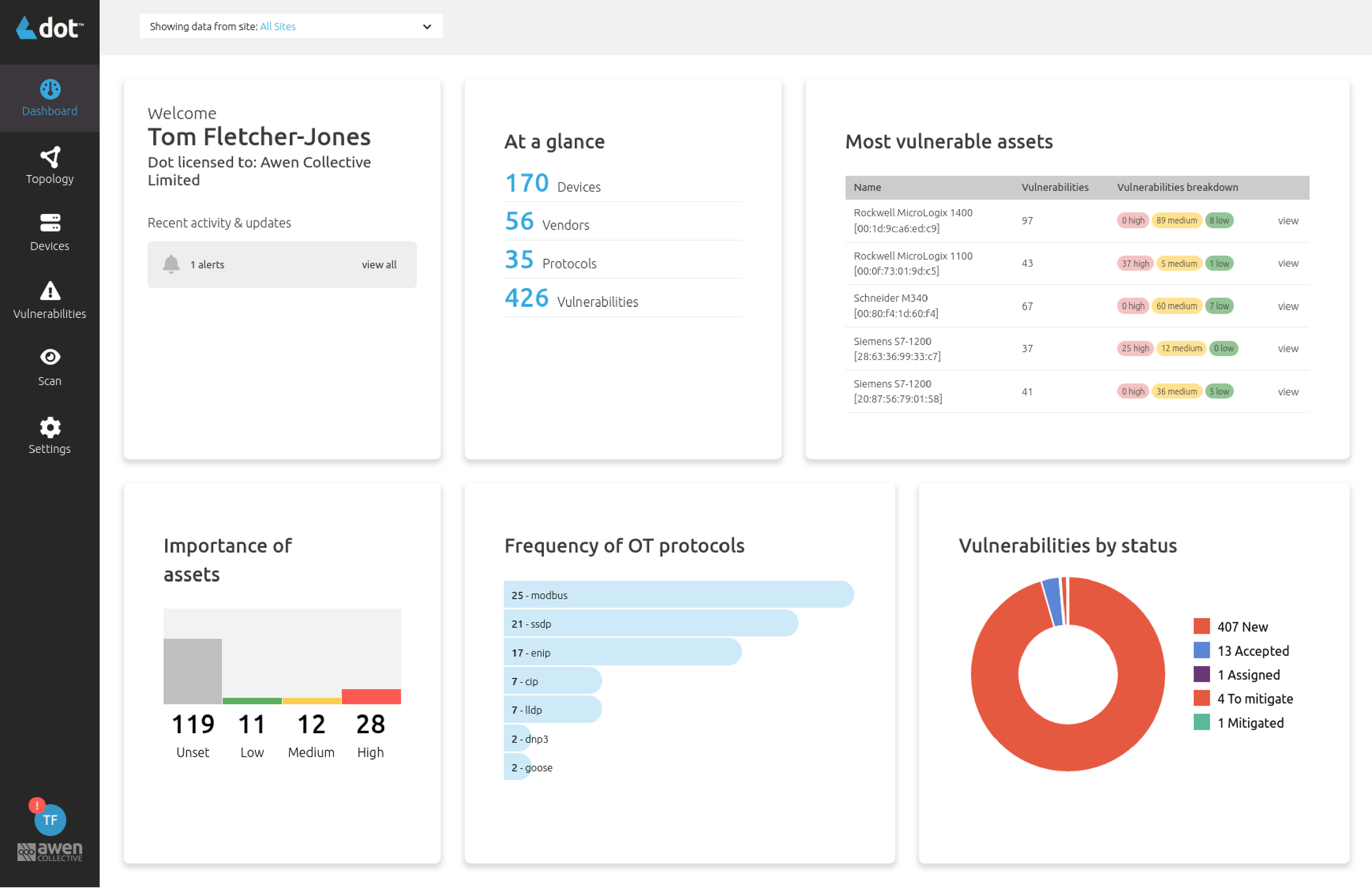
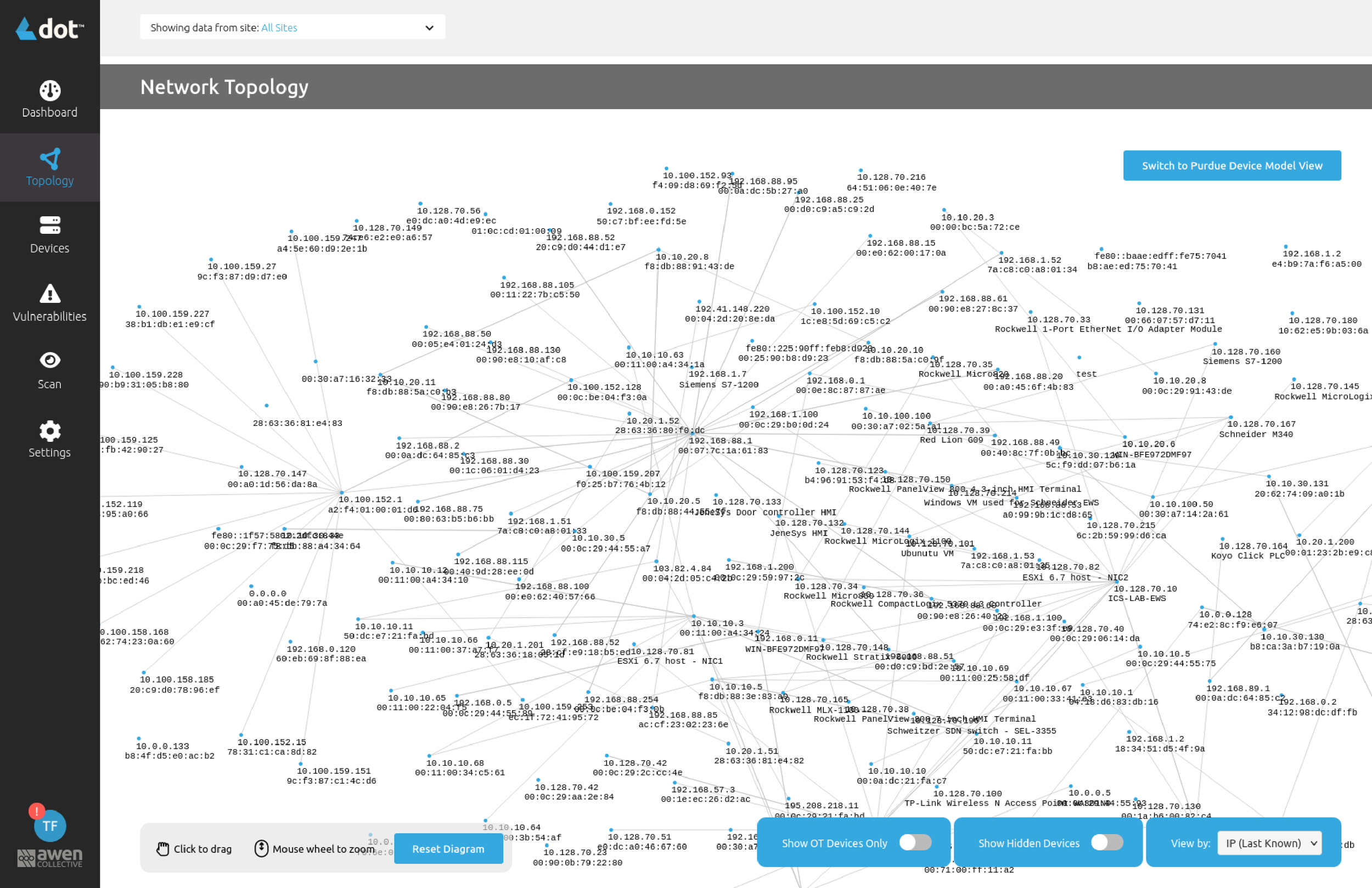
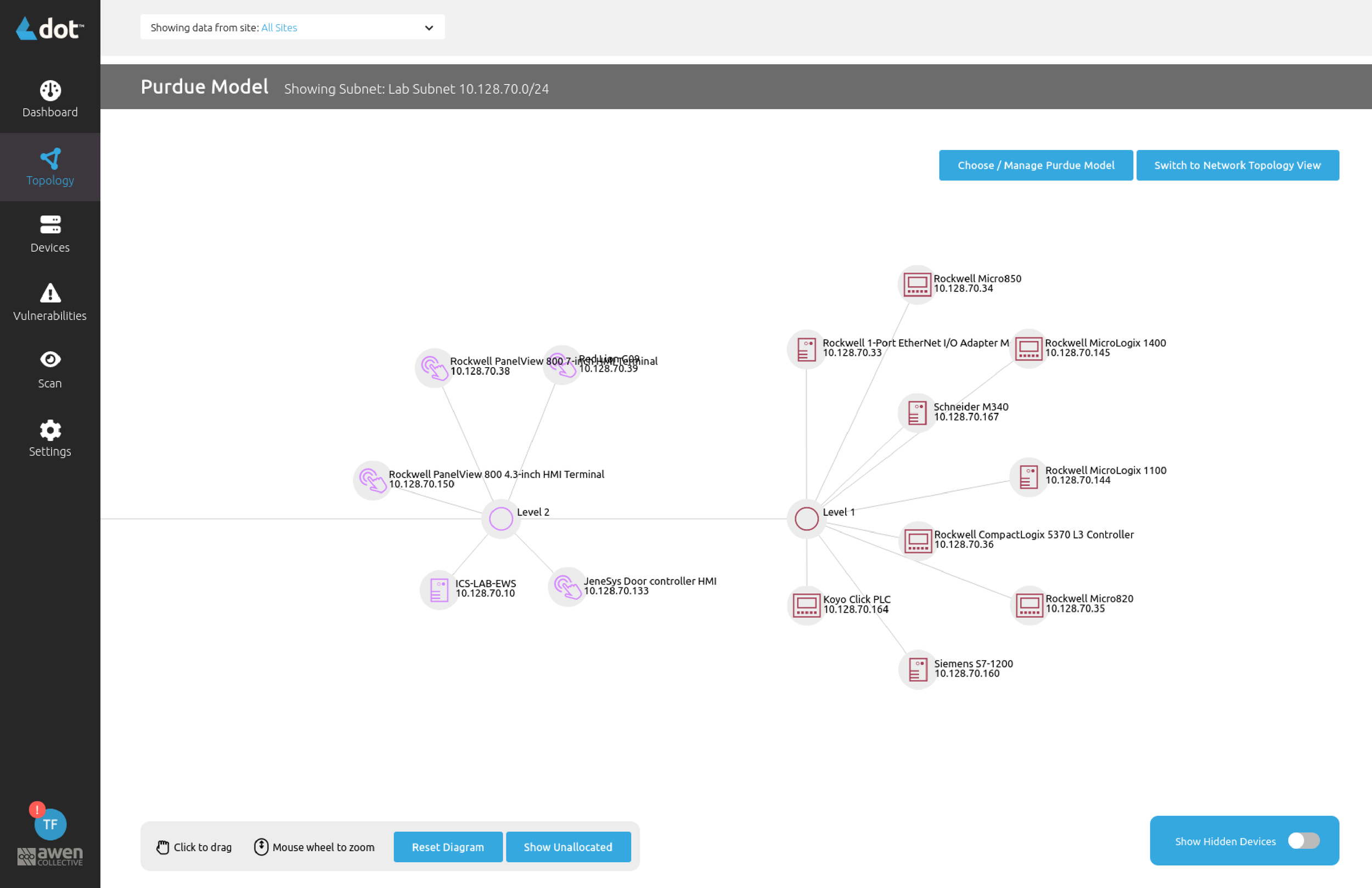
The first step in effectively identifying potential cyber threats of your modern and legacy operational infrastructure.
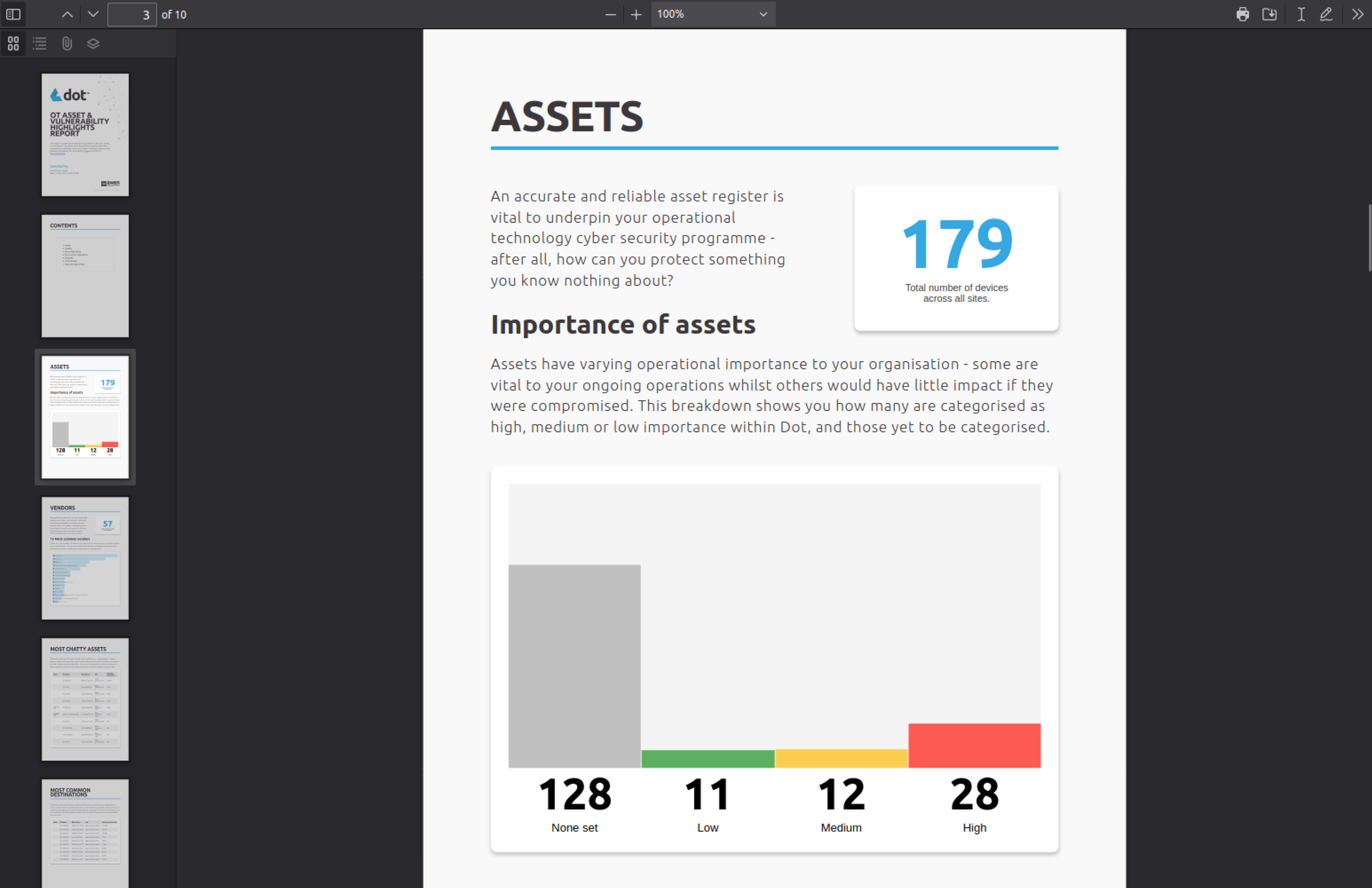
Identify OT Assets
Discover Vulnerabilities
Understand and Reduce Cyber Risk
Built from the ground up for use in OT environments, mindful of their constraints and key challenges.